In the current digital era, authentication has become a crucial defense line for safeguarding application security and user data privacy. From fledgling small startups to large-scale commercial platforms, all require a stable and reliable authentication solution. As an open-source authentication framework, SuperTokens is rapidly gaining popularity among developers with its own advantages, providing efficient, secure, and easily integrated authentication services for various applications.
Definition and Positioning
SuperTokens focuses on simplifying the user authentication process for modern web and mobile applications while giving top priority to data security. In the commercial authentication service market, services like Auth0, Firebase Auth, and AWS Cognito hold important positions, and SuperTokens aims to be a strong open-source alternative to them. For developers and enterprises with limited budgets and a high demand for customized authentication functions, SuperTokens is undoubtedly an ideal choice.
Core Features
- Multi-Layered Security Mechanisms: SuperTokens strictly adheres to the latest security standards. At the data transmission level, it uses the HTTPS encryption protocol to build a secure data transmission channel. In the user authentication process, it adopts JWT signature technology to accurately identify user identities. In addition, it has a built-in strategy to resist CSRF attacks, comprehensively protecting user information security and minimizing the risk of data leakage.
- Cross-Platform Compatibility: It strongly supports a variety of mainstream programming languages and frameworks, such as Node.js, Python, React, and Vue. This means that no matter what technology stack developers use to build applications, they can seamlessly integrate SuperTokens into existing projects without worrying about technical adaptation issues.
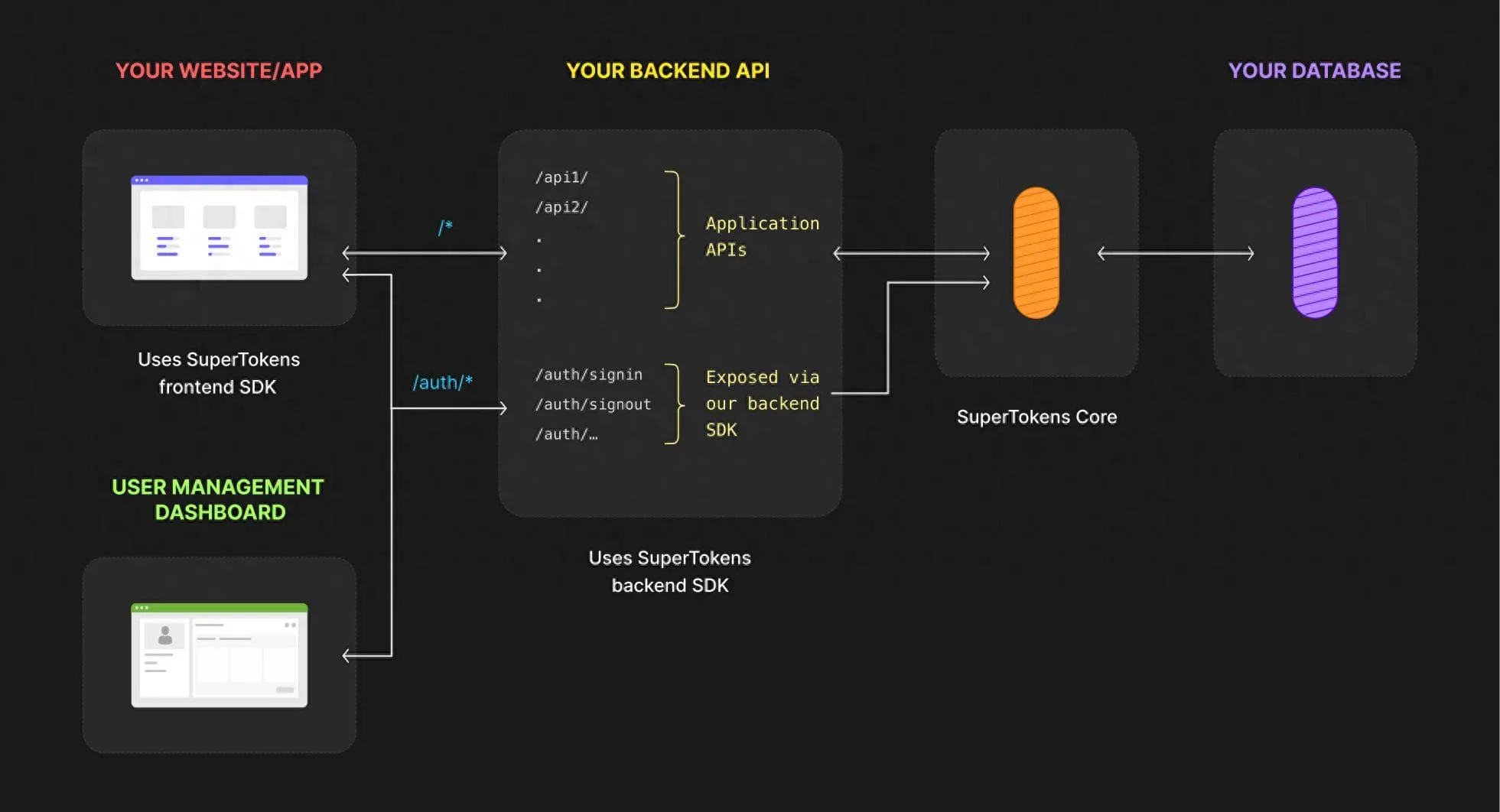
- Zero-Trust Architecture Design: Carefully constructed based on the microservices concept, SuperTokens has strong environmental adaptability. Whether it is a local environment, a cloud environment, or a hybrid environment, it can operate stably and consistently provide uniform authentication services, easily coping with complex and diverse application scenarios.
- Easy Integration: SuperTokens is equipped with rich SDKs and APIs. Developers only need to perform a few simple steps, and they can add complete authentication functions to their applications in just a few minutes. This greatly shortens the development cycle, reduces development costs, and makes the development work more efficient.
- Scalability: Developers can customize plugins according to actual business needs, flexibly adjusting or strengthening the default functions of SuperTokens to meet the personalized authentication requirements of applications in different industries and of different scales.
Technical Implementation
- Three-in-One Authentication: SuperTokens skillfully integrates three common authentication methods: email verification, password verification, and social login. This design provides users with a wide range of login options, fully considering the usage habits and security preferences of different user groups.
- Stateless Session Management: It uses JWT tokens for session management. This method not only effectively reduces the operating burden on the server but also significantly improves the scalability of the system. Even in high-concurrency scenarios, the application can run stably, bringing a smooth user experience.
- Real-Time Update Mechanism: Once there is a change in user information, the system will automatically trigger a real-time update to ensure that the data in various modules and services remains consistent, avoiding security risks and business errors caused by data asynchrony.
Application Scenarios
- E-commerce Field: In e-commerce platforms, users' payment details, shipping addresses, shopping cart data, etc., are all sensitive information. SuperTokens can effectively protect the security of this information, prevent user accounts from being stolen, and safeguard every transaction, thereby enhancing users' trust in e-commerce platforms.
- Social Media Platforms: Social media platforms handle massive user registration and login requests every day and also need to maintain complex social network connections. With high performance and high security, SuperTokens ensures the stable operation of the platform while strictly protecting users' social relationships and personal privacy from being leaked.
- Collaboration Platforms: Collaboration platforms need to strictly manage user access rights to ensure that only authorized users can access specific content. The detailed permission control function provided by SuperTokens effectively assists enterprises and teams in achieving secure and efficient collaboration.
- Enterprise Applications: Whether they are internal enterprise office applications or B2B applications, they all rely on reliable authentication services. SuperTokens builds a strong security barrier for enterprise applications, ensuring the confidentiality and integrity of enterprise data.
Community Support and Development
Behind SuperTokens is a vibrant developer community. Here, community members can exchange usage experiences, share development skills, and deeply participate in the development and improvement of the project. Continuous community support enables SuperTokens to keep up with the trend of technological development, constantly iterate and update, and promptly fix potential problems, providing users with better services.
In general, SuperTokens has created an excellent authentication solution for developers with its powerful functions, excellent security, and good scalability. Whether you are a startup team just starting out or a mature enterprise looking to optimize its existing authentication system, SuperTokens is worth a try. It can help you focus more on the development of core business logic and create secure and reliable applications.